It is a grim reality that cybersecurity teams have to face the dilemma of choosing the right alert to deal with, usually from some random threat classifications shown by siloed tools. They cannot assess every alert to identify a severe attack. With the regularity and diversity of attacks gaining speed, security teams are only getting more overwhelmed with alerts. As a result, many alerts are ignored, and most incidents go uninvestigated, making the organization highly vulnerable to attacks.
This challenge can be addressed by strengthening incident response capabilities through Security Orchestration, Automation, and Response (SOAR). Security analysts can use the SOAR platform to monitor data from various tools such as SIEM and threat intelligence platforms. SOAR minimizes manual intervention by collecting security data, prioritizing threats, and automating threat responses.
SOAR is a scalable, analyst-friendly, unified security platform solution that offers intelligence reports by automating data collection into a centralized location. Analysts can review this data, decide if the incident is suspicious, and initiate a playbook to respond to incidents.
A playbook is a set of remedial actions that can automate and orchestrate threat responses. It can be widely used to deal with recurring alerts and incidents. Made to run, either manually or automatically, playbooks can respond to specific alerts and incidents set by analytics or automation rules. Playbooks are predestined automated actions and can be altered to execute complex response actions.
Here are a few common scenarios where playbooks are used.
- Identifying high-risk devices within a network and restoring them to an approved state.
- Investigating and responding to malicious intruders/files to block phishing attempts.
- Disabling the network account of an employee who has left the organization.
- Periodically analyze the network and define ways to detect an attack.
- Act during a cybersecurity incident and ensure remediation to restore services.
Playbooks vary based on the threat and ensure the SOC executes every security process uniformly. By streamlining cumbersome processes, playbooks automate mundane, repetitive tasks and empower analysts to focus on strategic tasks that demand intelligent human interventions. From integrating cybersecurity solutions to determining custom workflows, playbooks offer considerable gains in productivity and efficiency across security operations.
Advantages of SOAR playbooks
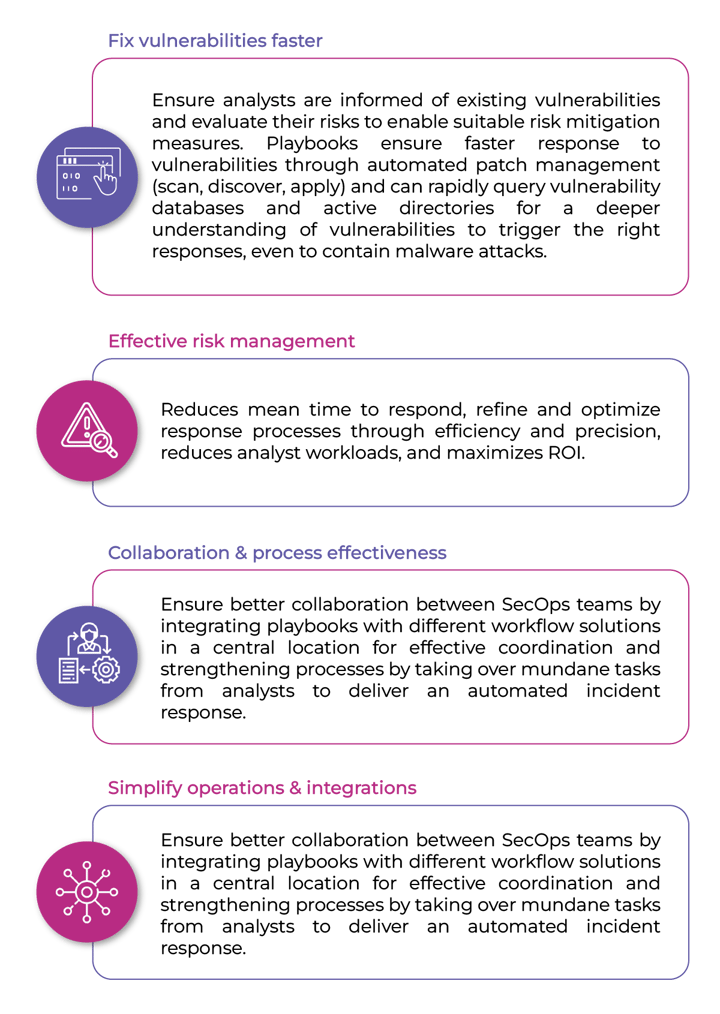
Maximize response with playbooks
Incident response is an immediate, fast activity that requires strong, consistent processes. Playbooks are the way to maximize the robustness of incident response as it refines the knowledge and experience of security analysts into a reliable and repeatable process that can handle the incident in the right manner to ensure proper remediation.
- Validate alerts quickly, enabling SOC teams to deal with alerts that matter.
- Capture experiential knowledge & quickly sensitize recruits to the technology environment.
- Adapt to changing offense tactics of attackers by updating playbooks for greater agility.
- Auditable nature of playbooks enables teams to identify bottlenecks due to changes caused by automation or configurations.
- Allows maximal detailing of threat data such as types, frequency of occurrence, analyst involved in working with the threat/action taken and threats marked as false positive, etc. to empower analysts to make the right decisions.
- Enables analysts to rapidly reference threats by the level of risk and exemplifies whether the risk is normal or abnormal.
Playbooks are an ideal way to improve the cybersecurity team’s ability to respond to cyber incidents. It can drive collaboration amongst teams for faster incident remediation. It clarifies by critically classifying the threat with specific incident scenarios and gives you the right direction to know the impact of the breach. A skilled and experienced team is necessary to develop, own, execute and manage a good playbook. You also need a deeper understanding of your networks, evolving threat landscape, and detection and response techniques to create playbooks that are adaptable and aligned to the risk levels of the organization.